Prioritizing Software & Firmware Vulnerabilities with CISA KEV
Taking an “inside-out” approach to XIoT (the Extended Internet of Things — IoT, OT, IoMT, and other typically unmanaged connected devices) vulnerability management can be a daunting task.
As we previously explored in another blog post, analyzing the proverbial “black box” of XIoT firmware can yield hundreds of previously unknown vulnerabilities, making the ability to assess and prioritize vulnerabilities critical for effective remediation.
The Cybersecurity and Infrastructure Security Agency (CISA) introduced the Known Exploited Vulnerabilities (KEV) Catalog as part of BOD-22-01 to help organizations prioritize their remediation efforts effectively. In this blog post, we will dive into why CISA Known Exploited Vulnerabilities matter for vulnerability management programs and how the NetRise Platform integrates this data to help with XIoT vulnerability prioritization efforts.
The Significance of CISA Known Exploited Vulnerabilities in XIoT Devices
One of the most common struggles organizations have with vulnerability management programs is deciding which vulnerabilities to address first. The sheer number of vulnerabilities found is often overwhelming and it can be incredibly difficult to know where to start. The KEV Catalog helps streamline the prioritization process by highlighting vulnerabilities that are actively being exploited by threat actors, which acts as a high fidelity signal in a sea of noise. CISA directly comments on this with the following statement in BOD-22-01:
Known exploited vulnerabilities should be the top priority for remediation. Based on a study of historical vulnerability data dating back to 2019, less than 4% of all known vulnerabilities have been used by attackers in the wild. Rather than have agencies focus on thousands of vulnerabilities that may never be used in a real-world attack, BOD-22-01 shifts the focus to those vulnerabilities that are active threats.
CISA further suggests all organizations can benefit from focusing on vulnerabilities in the KEV Catalog, not just those bound by BOD-22-01:
Although not bound by BOD 22-01, every organization, including those in state, local, tribal, and territorial (SLTT) governments and private industry can significantly strengthen their security and resilience posture by prioritizing the remediation of the vulnerabilities listed in the KEV catalog as well.
The KEV Catalog was initially published November 2021 with 291 CVEs. As of the writing of this blog post, that number has increased to 980 CVEs to keep pace with the ever-evolving threat landscape. This growth reflects the speed at which threat actors change their tactics to evade the latest detection techniques, making it even more crucial for organizations to stay vigilant and prioritize remediation efforts based on active threats. The important thing to remember is not all CVEs added to the KEV are brand new. In many cases, threat actors will make use of old vulnerabilities that may have been overlooked by time-based vulnerability management programs. For example, in June 2023, 2 CVEs from 2019 targeting D-Link devices were added to the KEV Catalog.
Some organizations may be weary of utilizing the KEV Catalog as a data point because it covers such a wide range of vulnerabilities and devices. Specifically, any CVE can make it into the KEV Catalog, whether it be a vulnerability in an Apple device, a Microsoft operating system, or a firewall. Despite this wide scope, XIoT device manufacturers and asset owners have a responsibility to pay attention to the vulnerabilities added to the KEV Catalog. In 2022, approximately 30% of CVEs in the KEV Catalog affected XIoT devices or software components commonly used by XIoT devices. As of the writing of this blog post in August 2023, that number has shifted to about 20%.
The NetRise Platform Simplifies Vulnerability Management for XIoT Devices
As previously mentioned, vulnerability management is not about attempting to remediate every single vulnerability but rather about understanding the risks each vulnerability introduces to an organization. The KEV Catalog provides an extremely high-confidence reference for prioritization. NetRise integrates this data with other critical data points, allowing organizations to comprehensively assess and understand the potential impact of vulnerabilities.
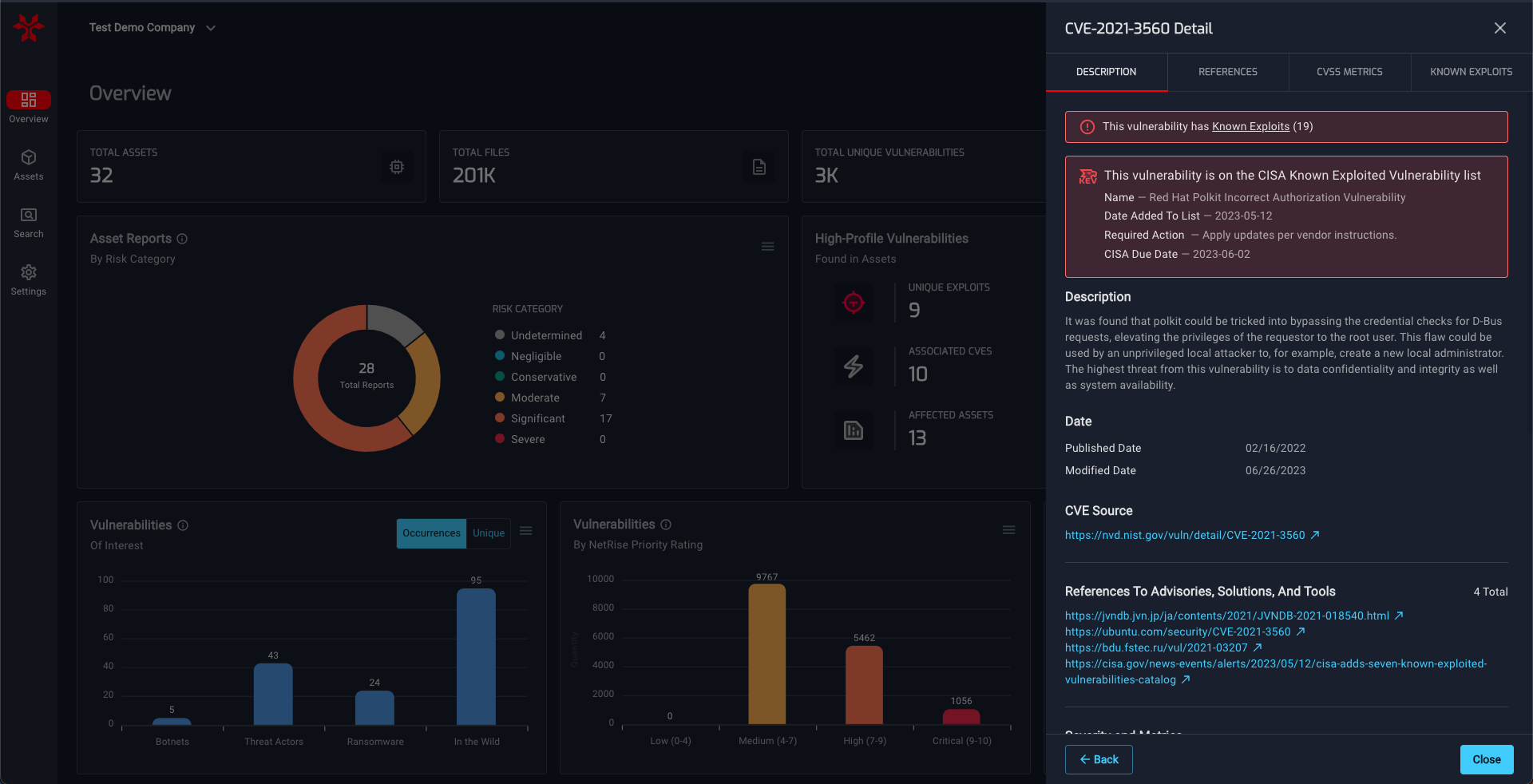
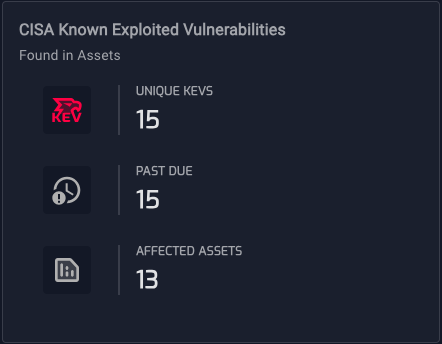
NetRise goes beyond the KEV Catalog to strengthen vulnerability management efforts. By considering whether a vulnerability is known to be leveraged by botnets, ransomware groups, or other threat actors, organizations gain further insights into the severity of a vulnerability. Additionally, vulnerabilities with widely recognized "marketing" names, such as Heartbleed or Shellshock, signal heightened attention from the security community and should be prioritized accordingly. NetRise also helps identify whether an exploit is available and whether it has been weaponized, providing organizations with a comprehensive understanding of the threat landscape.
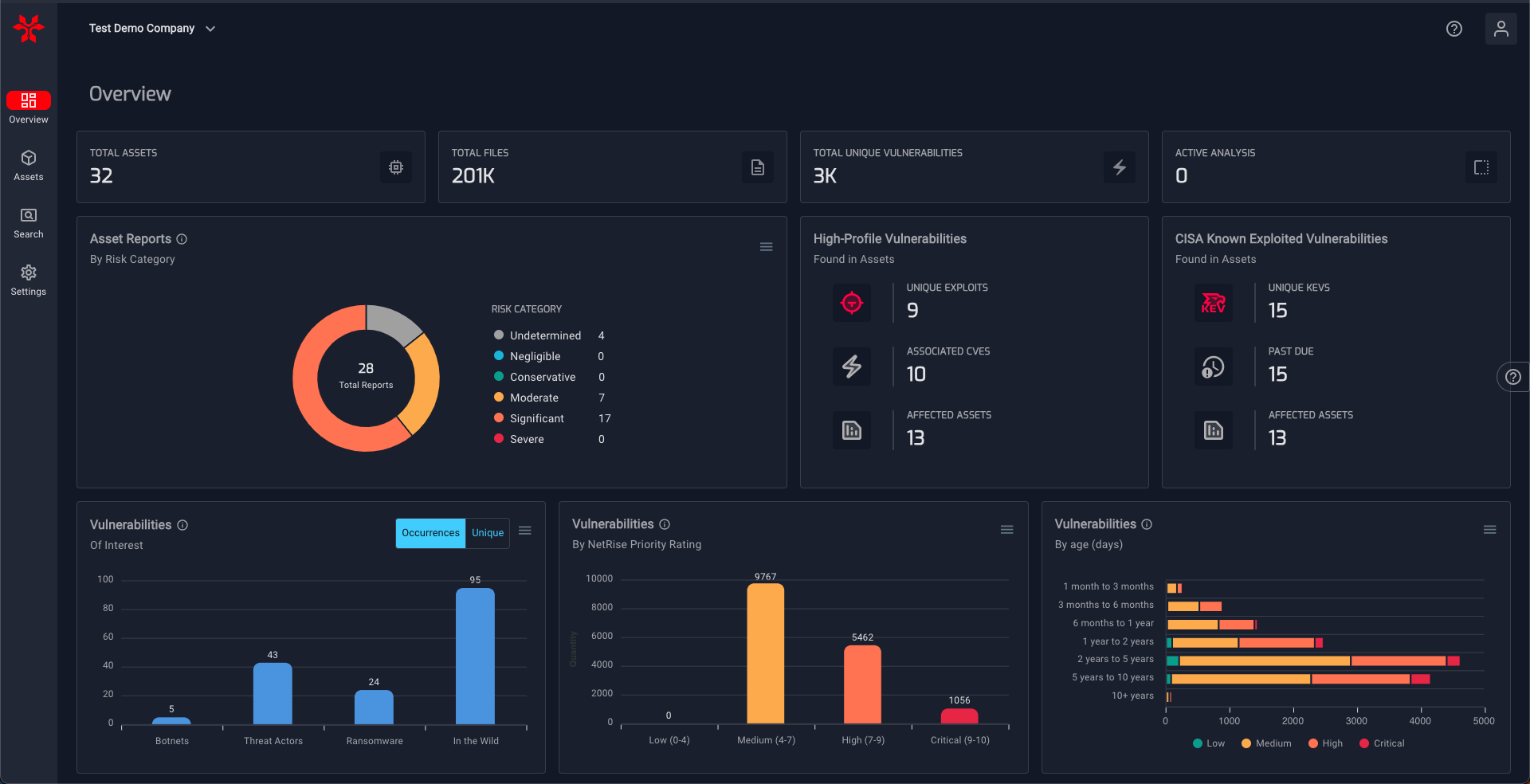
NetRise's user-friendly dashboard provides an intuitive summary of the KEV Catalog, allowing organizations to quickly identify vulnerabilities affecting their XIoT devices. By offering granular insights at the individual asset and software component levels, NetRise empowers organizations to pinpoint affected areas and prioritize remediation efforts effectively. Answering the crucial question, "Am I affected by the latest Known Exploited Vulnerability?" becomes effortless, enabling organizations to take immediate action and bolster their security posture.
Stay up to date with the news
Sign Up To Get Our Free Insights Delivered To Your Inbox




