Integrate with NetRise
NetRise integrates seamlessly into your workflows, whether it's bringing your software into our system, outputting findings into your vulnerability and threat management systems, or into your CI/CD pipeline and SOC workflows. With NetRise and our partners, you'll accelerate the prioritization, remediation, and mitigation of risk associated with your software supply chain.
Threat Management
Ready to build robust binary composition analysis into your software development and third-party risk management programs?
Frequently Asked Questions
How we Integrate with other tools?
Help security teams tackle system weaknesses before they can be exploited by attackers. Also, allow ethical hackers to evaluate these vulnerabilities to improve the organization's security. This proactive strategy reduces risks and promotes ongoing enhancement of security practices.
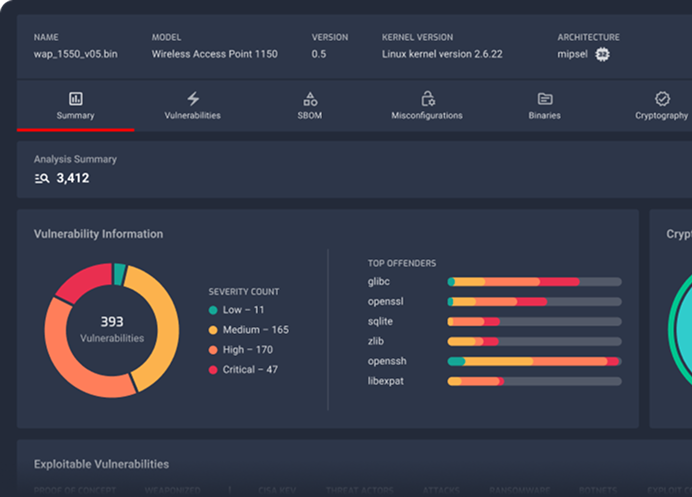
How NetRise Analyze Software Builds for Weaknesses?
Identifying and managing potential risks proactively is essential, especially before vulnerabilities are exploited. Decompiling binaries on a large scale helps us analyze and detect weaknesses in the code, allowing us to address issues before malicious actors can take advantage.
How NetRise Analyze Software Builds for Weaknesses?
Identifying and managing potential risks proactively is essential, especially before vulnerabilities are exploited. Decompiling binaries on a large scale helps us analyze and detect weaknesses in the code, allowing us to address issues before malicious actors can take advantage.
How we Integrate with other tools?
Help security teams tackle system weaknesses before they can be exploited by attackers. Also, allow ethical hackers to evaluate these vulnerabilities to improve the organization's security. This proactive strategy reduces risks and promotes ongoing enhancement of security practices.
How we Integrate with other tools?
Help security teams tackle system weaknesses before they can be exploited by attackers. Also, allow ethical hackers to evaluate these vulnerabilities to improve the organization's security. This proactive strategy reduces risks and promotes ongoing enhancement of security practices.
How NetRise Analyze Software Builds for Weaknesses?
Identifying and managing potential risks proactively is essential, especially before vulnerabilities are exploited. Decompiling binaries on a large scale helps us analyze and detect weaknesses in the code, allowing us to address issues before malicious actors can take advantage.

