NetRise Trace: AI-Powered Intent-Based Vulnerability Search
Product security professionals continually seek innovative methods to better protect their consumers in the ever-evolving cybersecurity landscape. While still relevant, traditional approaches often fall short in the face of sophisticated modern cyber threats. This is where NetRise Trace, with its groundbreaking AI-powered intent-driven search technology, transforms how we safeguard products. This blog post delves into how NetRise Trace enables product security teams to bolster their defenses and provide enhanced consumer security.
Understanding NetRise Trace: A Game-Changer in Vulnerability Management
NetRise Trace isn’t your typical security tool. It transcends conventional signature-based vulnerability search methods, focusing instead on the underlying motives or purposes behind code and configurations. This AI-driven approach allows security teams to identify vulnerabilities by understanding the intent of malicious actors or negligent developers. The NetRise Platform analyzes the entire system, and NetRise Trace enables quick and easy search across the multitude of insights provided. The greater utility and efficiency of this powerful search capability enables comprehensive vulnerability identification across a wide range of software packages, misconfigurations, and unidentified flaws. Trace maps out the intricate relationships between components in the software supply chain, producing an easy to comprehend visualization.
How Product Security Teams Can Utilize NetRise Trace
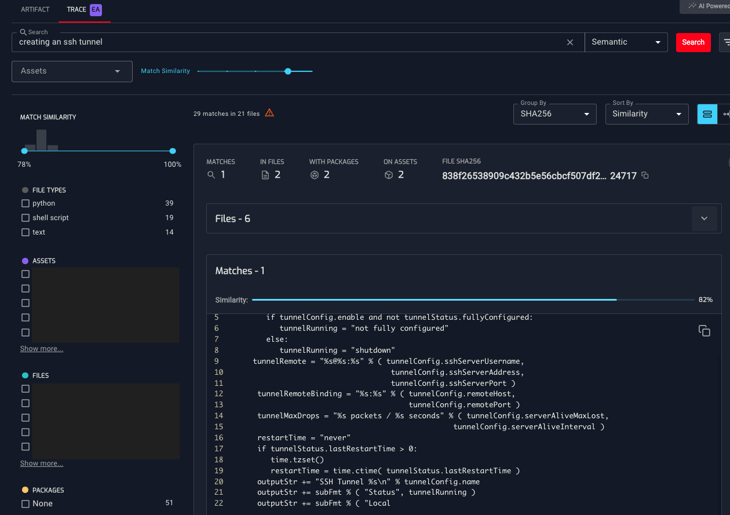
1. Intent-Based Vulnerability Searches
Instead of searching for specific code patterns, product security teams can query for behaviors and configurations that indicate security risks. For instance, a query like "creating an ssh tunnel" — while SSH tunnels are a secure method of transferring data, they can be a double-edged sword if not set up correctly or used for unauthorized access.
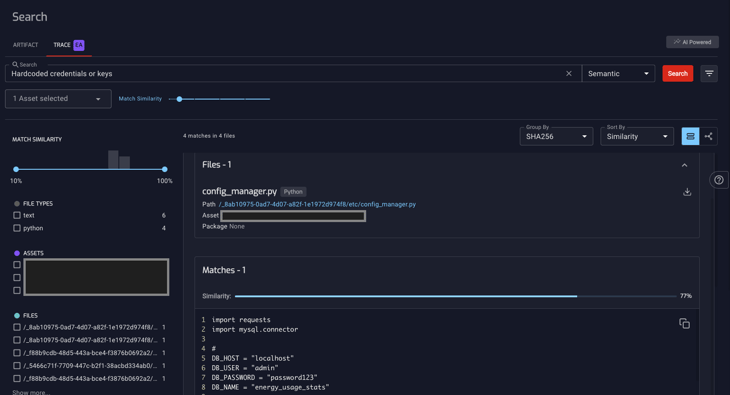
2. Hardcoded credentials or keys
Hardcoded credentials, such as passwords or encryption keys, can pose a significant security risk if exposed.
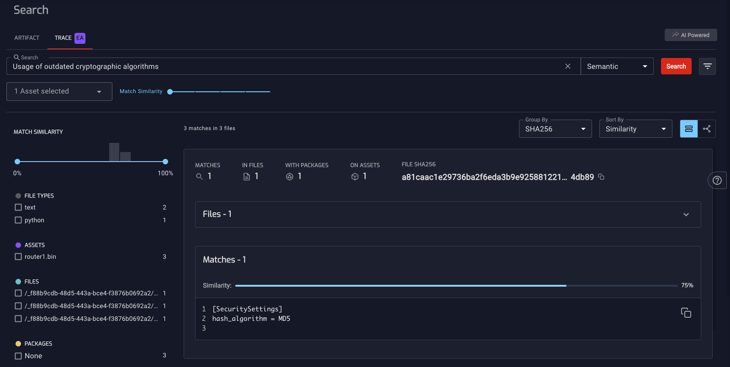
3. Detecting Weak Cryptographic Practices
NetRise Trace excels in identifying weak or flawed cryptographic implementations often overlooked in standard analyses. By searching for "usage of outdated cryptographic algorithms" or "weak encryption algorithms", Trace can uncover vulnerabilities like the use of outdated encryption techniques (e.g., MD5, SHA-1) or improper key management practices. These insights are crucial for strengthening the overall security of software, ensuring that data protection measures are robust and current.
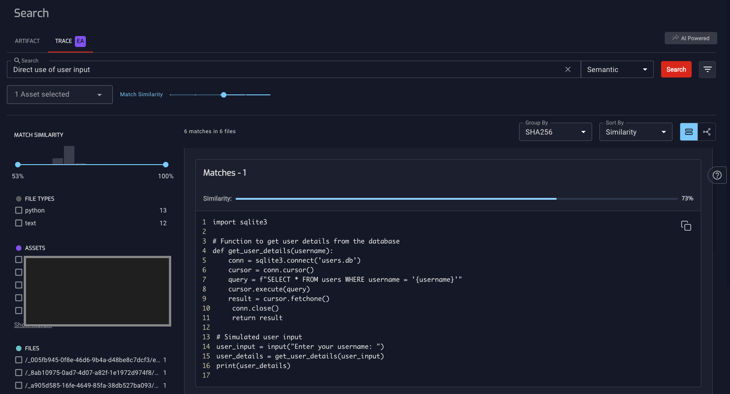
4. Uncovering Vulnerable User Input Handling
“Direct use of user input” in code. This search is crucial for uncovering places where user input might flow into critical operations without checks, potentially leading to security vulnerabilities like SQL injection, XSS, etc. It’s all about ensuring user input is handled safely and securely.
Real-World Examples of NetRise Trace in Action
Example 1: IoT Device Security
An IoT device manufacturer used NetRise Trace to search for "API endpoints exposed without adequate authentication”.
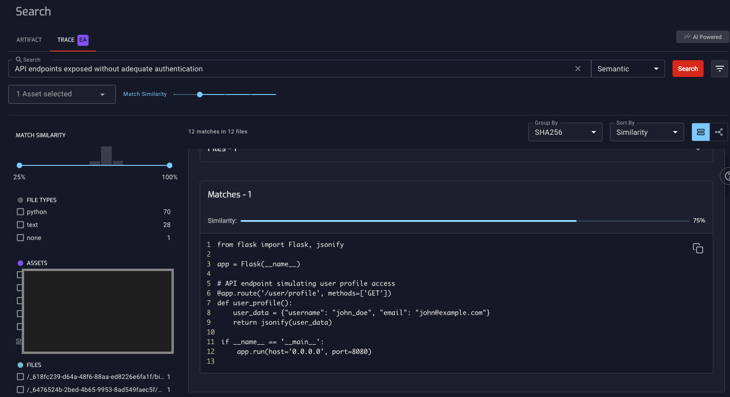
Trace uncovered a previously unknown vulnerability in how the device handled API calls, leading to an immediate security patch.
Example 2: Industrial Control Systems
In an industrial control system, NetRise Trace was employed to look for "usage of Modbus/TCP, EtherNet/IP, Siemens S7 without security controls in configuration".
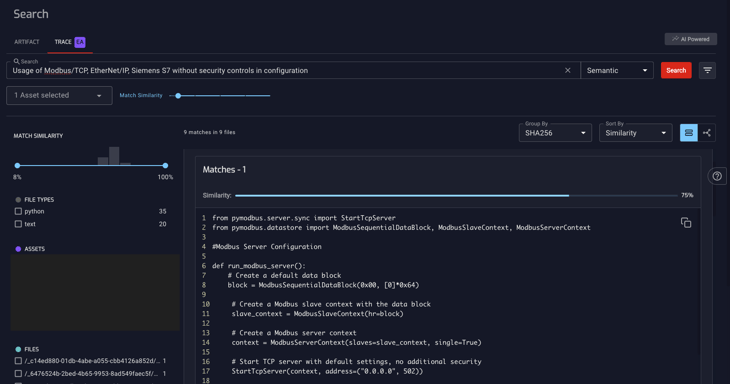
The search pinpointed a critical oversight in securing a Modbus server.
Producing More Secure Products with NetRise Trace
In an era where digital safety is paramount, NetRise Trace revolutionizes how product security teams address vulnerability detection and remediation. By harnessing the advanced capabilities of AI, NetRise Trace delves deep into the intricacies of code and configurations, unraveling the intentions behind them. This approach is not just about identifying vulnerabilities; it's about understanding the nuances of potential security threats, providing a more comprehensive landscape for security analysis.
As the complexity and sophistication of cyber threats increases, the traditional reactive approach to security is no longer sufficient. The utilization of Trace in the NetRise Platform enables teams to "shift left", embedding security into the earliest stages of product development. This proactive stance ensures vulnerabilities are identified and addressed before they can be released into the wild, significantly reducing the risk of exploitation.
This shift in approach is crucial in a landscape where consumer trust is hard-earned and easily lost. In the hands of product security professionals, NetRise Trace becomes more than a tool — it transforms into a beacon of trust and integrity. It empowers teams to produce functional and secure products, fortifying the bond between consumers and brands in an increasingly digital world.
By integrating NetRise Trace into their product security processes, product teams are not just enhancing the security of their products — they are reinforcing their commitment to consumer trust and safety. Every product is a testament to a company's values, and NetRise Trace stands as a testament to the value NetRise places on security, trust, and integrity.
Stay up to date with the news
Sign Up To Get Our Free Insights Delivered To Your Inbox




