Illuminating the Dark Corners: Unveiling KEVs in Enterprise IoT and Network Devices
In the ever-complex domain of cybersecurity, there’s a new player that's commanding attention: Known Exploited Vulnerabilities, or KEVs. These are vulnerabilities that cybercriminals are actively exploiting, and they represent a clear and present danger. Yet, they often hide in the least expected places — within the firmware of networking and IoT devices which form the bedrock of enterprise infrastructure. Our recent addition of KEV analysis to the Netrise Platform marks a significant leap forward in unveiling these hidden threats.
What are KEVs?
Known Exploited Vulnerabilities, as defined by the Cybersecurity and Infrastructure Security Agency (CISA), are vulnerabilities observed to be used in attacks. These aren’t theoretical risks; they are the cracks adversaries actively exploit to breach systems. Understanding and mitigating KEVs is not just recommended; it’s crucial for robust cybersecurity.
The Silent Risk in Firmware and IoT
For too long, firmware in IoT devices and traditional networking devices have been the 'black boxes' of the enterprise world — crucial to operations yet opaque and too often ignored from a security standpoint. These devices, from network routers to smart environmental controls, are operational workhorses but can also be Achilles' heel if their vulnerabilities are left unaddressed.
Our Platform’s KEV Analysis: A Deep Dive into Firmware
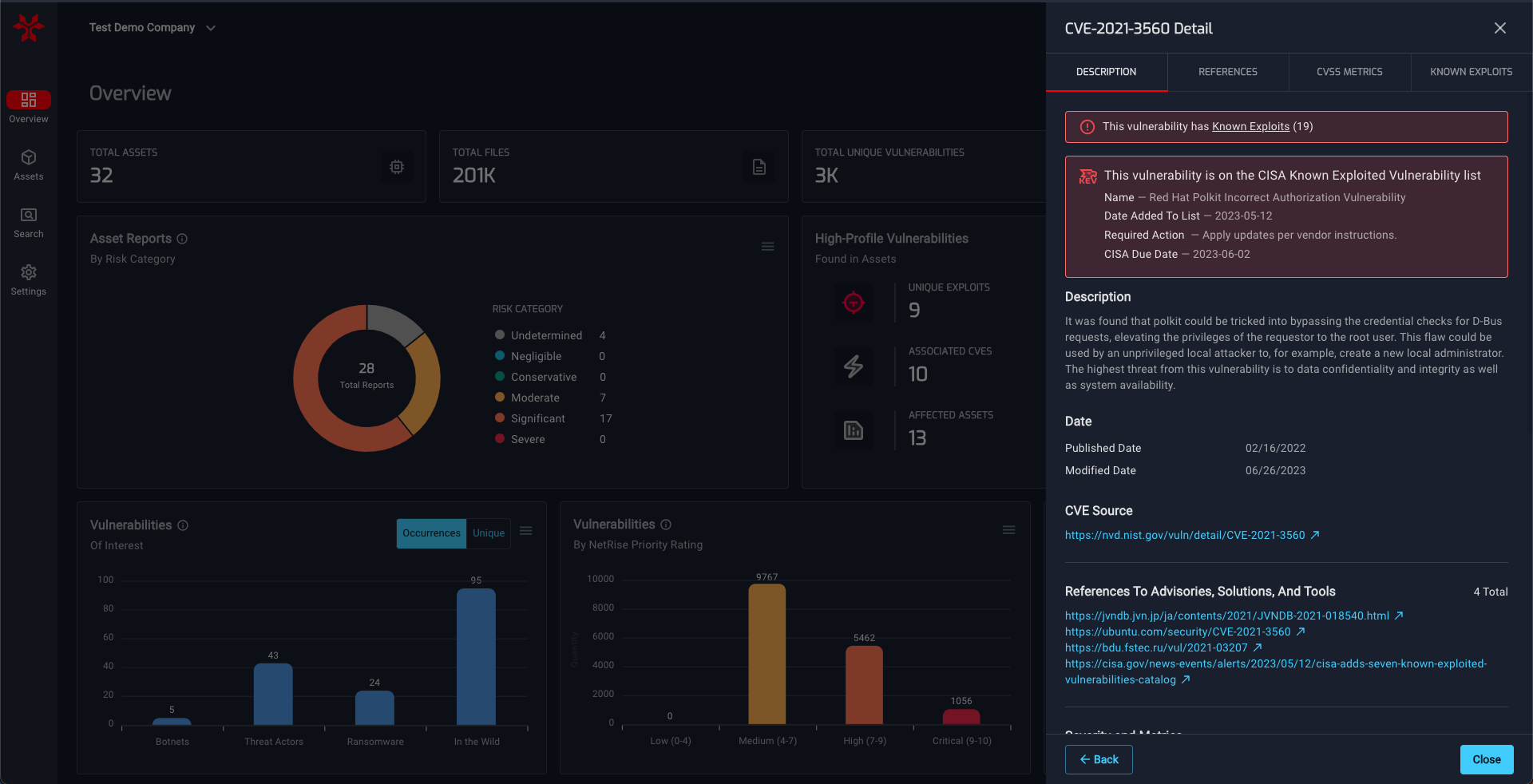
Our platform’s recent feature addition — KEV analysis — is a game-changer. By decompiling and dissecting firmware, we’re not just listing potential vulnerabilities; we’re pinpointing the ones being actively exploited. Here’s what our analysis reveals:
Percentage of Firmware with KEVs: Our analysis shows that 50% of all the firmware analyzed by the Netrise Platform contains KEVs. This is a stark reminder of the pervasive nature of these exploited vulnerabilities.
Number of Unique CISA KEVs: Across all firmware, we identified 35 unique KEVs.
Most Common CISA KEVs: Our platform identifies the KEVs that are most frequently exploited, providing a clear priority list for remediation efforts.
Oldest CISA KEVs: Alarmingly, some KEVs have been lurking for years. We highlight the oldest overdue ones, underscoring the critical need for updates.
|
KEV_ID |
AddedDate |
DueDate |
DaysOverDue |
|
CVE-2020-1472 |
11/3/2021 0:00:00 |
9/21/2020 0:00:00 |
1136 |
|
CVE-2021-40438 |
12/1/2021 0:00:00 |
12/15/2021 0:00:00 |
686 |
|
CVE-2021-44228 |
12/10/2021 0:00:00 |
12/24/2021 0:00:00 |
677 |
|
CVE-2022-26485 |
3/7/2022 0:00:00 |
3/21/2022 0:00:00 |
590 |
|
CVE-2022-26486 |
3/7/2022 0:00:00 |
3/21/2022 0:00:00 |
590 |
|
CVE-2016-5195 |
3/3/2022 0:00:00 |
3/24/2022 0:00:00 |
587 |
|
CVE-2019-11043 |
3/25/2022 0:00:00 |
4/15/2022 0:00:00 |
565 |
|
CVE-2012-1823 |
3/25/2022 0:00:00 |
4/15/2022 0:00:00 |
565 |
|
CVE-2021-3156 |
4/6/2022 0:00:00 |
4/27/2022 0:00:00 |
553 |
|
CVE-2021-22600 |
4/11/2022 0:00:00 |
5/2/2022 0:00:00 |
548 |
Components Most Affected by KEVs: Identifying the components most at risk, like Firefox, makes you question why a vendor would even have that component on a device.
|
Component Name |
Component Version |
Number of KEVs |
|
firefox_esr |
32.0.3 |
9 |
|
linux_kernel |
2.6.23.1 |
8 |
|
linux_kernel |
2.6.31 |
8 |
|
linux_kernel |
2.6.32.49 |
8 |
|
linux_kernel |
2.6.22 |
8 |
|
linux_kernel |
2.6.27.13 |
8 |
|
linux_kernel |
2.6.22.19 |
8 |
|
linux_kernel |
2.6.23 |
8 |
|
linux_kernel |
2.6.24 |
8 |
|
linux_kernel |
2.6.35.12 |
8 |
The Power of Visibility and Proactive Defense
Understanding the presence of KEVs in firmware across IoT and traditional networking devices is a transformative step in cybersecurity. It’s not enough to know what could go wrong; it’s about knowing what is likely being targeted right now. Our platform not only illuminates these risks but also empowers enterprises to take proactive, informed actions. Regular analysis, staying ahead of patches, and a proactive security strategy are no longer optional; they are the keys to turning potential vulnerabilities into pillars of security.
Incorporating KEV analysis into our binary/firmware analysis platform is more than just a feature update; it’s a paradigm shift. It’s about bringing hidden dangers into the spotlight and equipping enterprises with the knowledge and tools to act decisively. Remember, in the digital world, the unseen doesn’t have to remain unknown. With KEV analysis, we’re not just shining a light on vulnerabilities; we’re guiding enterprises on the path to robust, resilient cybersecurity.
To see the NetRise Platform in action for yourself, request a demo today.
Stay up to date with the news
Sign Up To Get Our Free Insights Delivered To Your Inbox
You might also like
Explore other exciting events!




