The NPM Supply Chain Attack Was No Log4j, But It Could Have Been
On September 8, 2025, attackers compromised more than 20 NPM packages—including chalk, debug, ansi-styles, ansi-regex, color-string, and wrap-ansi—used in more than 2 billion weekly downloads. For over two hours, every new installation carried malware designed to steal cryptocurrency by interpreting and redirecting wallet transactions.
The attack began with a phishing campaign against maintainer Josh Junon (Qix). A spoofed support domain prompted him to provide his credentials, allowing adversaries to publish the malicious updates. The injected code used a Levenshtein distance algorithm to subtly alter wallet addresses, replacing them with attacker-controlled versions that looked almost identical. The payload also checked for browser context and hooked into APIs such as window.fetch, XMLHttpRequest, and window.ethereum.request, enabling theft of cryptocurrency transactions in real time.
Although the financial fallout was minimal, researchers stress this was no trivial incident. Darren Meyer, security research advocate at Checkmarx Zero, noted in a Dark Reading article that the phishing attack was well executed, the malware technically accomplished, and the campaign appeared carefully managed. He praised Qix for acting transparently and quickly, pointing out that the developer community was fortunate to avoid a larger crisis.
This underscores a hard truth: organizations that rely on open-source packages, which is nearly every organization today, cannot assume the next incident will resolve so cleanly.
The Zero-Day Challenge
When a zero-day or software supply chain compromise emerges, the board and executive team will ask two immediate questions:
- Are we exposed?
- Where are we exposed?
Answering those questions means knowing:
- Which systems or devices are impacted
- Which components include the compromised packages
- How far the impact spreads across deployments and build pipelines
- Whether the compromised code is reachable via the network and can actually execute at runtime
Without immediate answers, you lose critical time distinguishing theoretical risk from the exposures that matter most. NetRise is built to give you those answers first.
How NetRise Determined if We Were Exposed to the NPM Attack
Imagine this: A zero-day strikes at 9 a.m., and by 9:15, you know whether you’re exposed, and where.
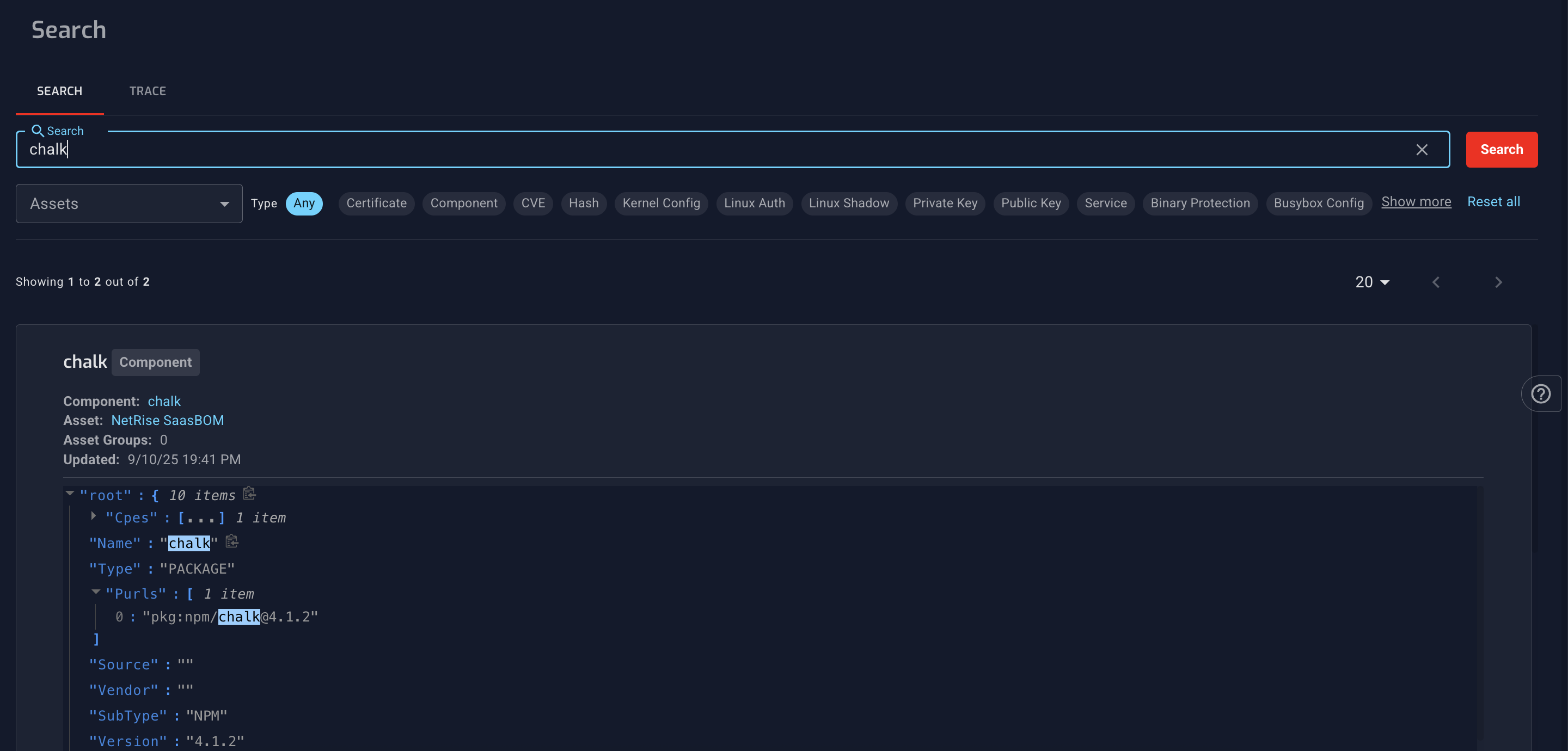
When the NPM package compromise was discovered, we immediately turned to NetRise's Search capabilities to assess our own exposure. Using our Artifact Search feature, we were able to instantly query across all our container images for the compromised packages with simple keyword searches that returned results in under a second.
We quickly discovered that we were not affected.
Takeaways from the NPM Supply Chain Attack
The NPM software supply chain attack highlights both ecosystem fragility and the need for defense-in-depth. Experts recommend several core practices:
- Maintain a private package repository.
- Use supply chain security tools that create accurate software inventories and detect compromise.
- Apply endpoint controls that limit the scope of impact when incidents occur.
These basics reduce exposure, but they leave a persistent question: where are you exposed? That visibility gap can decide whether you remediate quickly or face prolonged disruption.
How NetRise Changes the Equation
NetRise gives you immediate visibility into exposure, even during fast-moving zero-day events. Instead of relying on incomplete or vendor-supplied data, the NetRise platform analyzes the compiled software that actually executes in your environment.
- Map dependencies. Build complete, binary-derived inventories across software, containers, and packaged applications instantly, without waiting on vendors.
- Correlate threats. Cross-check exposure against vulnerability context, exploitability, and reachability to cut through the noise and identify real risk.
- See deployments. Pinpoint where compromised components load across build jobs, developer systems, and production environments before attackers can take advantage.
- Act with clarity. Prioritize fixes based on whether vulnerable code actually executes, so your first response addresses the most impactful exposures.
- Stay ahead. Detect anomalies such as hidden scripts, misconfigurations, or suspicious publishing behavior before they cascade into compromise.
NetRise doesn’t just improve best practices. It compresses the time from discovery to answer, giving you immediate visibility into whether, and where, you are exposed.
What’s Inside Your Software?
Software supply chain compromises no longer target only vulnerable code. They target the trust you place in the ecosystem itself. The September 8 NPM software supply chain event shows how quickly adversaries can exploit that trust at scale.
The browser-based interception also demonstrates why surface-level dependency checks are not enough. When malicious code can execute in any context where a package loads, you need visibility into what actually executes, not just what appears in source code.
With NetRise, you move beyond reaction to pinpoint exposure immediately, act with confidence, and restore operations before attackers can capitalize.
Stay up to date with the news
Sign Up To Get Our Free Insights Delivered To Your Inbox
You might also like
Explore other exciting events!




